Hot vs Cold Wallets: How Institutions Balance Liquidity and Security in Digital Asset Custody
When it comes to safeguarding digital assets, the debate between hot and cold wallets isn’t just technical — it’s strategic. For institutions, understanding the difference goes far beyond knowing which wallet is “online” or “offline.” It’s about how to manage liquidity, mitigate operational risk, meet regulatory expectations, and protect core reserves.
In this article, we unpack the fundamentals of hot and cold wallets, examine their tradeoffs through an institutional lens, and explain how B2Vault’s custody architecture blends the best of both worlds.
What Is a Hot Wallet?
A hot wallet is any wallet that maintains an active connection to the internet during key management or transaction signing.
Hot wallets are typically used for frequent transactions, such as day-to-day operations, settlement flows, or user withdrawals. Because they’re always “online,” they provide immediate access to assets, making them ideal for operational agility — but also more exposed to cyber threats.
Key characteristics of hot wallets:
- Online connectivity for signing and broadcasting transactions
- Ideal for rapid transfers, trading activity, and settlement flows
- Keys or signing components are held in connected environments (servers, APIs, or mobile devices)
- More vulnerable to phishing, malware, and hacking attempts
Hot wallets are the “operational layer” of a custody system — convenient, but they demand robust security hardening to defend against evolving cyber threats.
What Is a Cold Wallet?
A cold wallet is a wallet where the private keys or signing mechanisms are stored offline — typically on air-gapped devices or in secure physical vaults.
Transactions are prepared online, exported to the offline environment for signing, and then re-imported for broadcasting. This approach significantly reduces network attack surfaces, making cold wallets ideal for long-term storage of large asset reserves.
Key characteristics of cold wallets:
- Keys are generated and stored offline
- Signing occurs in air-gapped or physically secured environments
- Assets are moved infrequently and through controlled workflows
- Immune to most remote attacks, but require strong physical security and operational discipline
Cold wallets form the “strategic vault layer” of institutional custody — prioritizing maximum security over immediate liquidity.
Institutional Comparison: Hot vs Cold Wallets
| Dimension | Hot Wallet | Cold Wallet |
| Connectivity | Online | Offline / Air-gapped |
| Liquidity & Speed | Immediate | Requires procedural steps |
| Cybersecurity Risk | Higher exposure to online threats | Minimal online attack surface |
| Operational Complexity | Simple, automated | Procedural, manual approvals |
| Physical Security | Lower emphasis | Critical (vaults, HSMs, backups) |
| Regulatory Alignment | Best for active operations | Often required for reserves |
| Typical Use | Trading, settlement, user withdrawals | Long-term storage, reserves, treasury |
Why Institutions Use Tiered Wallet Structures
Leading custodians don’t rely exclusively on one type of wallet. Instead, they design tiered custody architectures that strategically blend hot and cold environments:
- Hot Tier (Operational Layer)
A small percentage of total assets is held in secure hot wallets to support daily withdrawals, trading, and settlements. - Cold Tier (Reserve Layer)
The majority of assets are held offline in cold vaults, secured by physical controls, air-gapped devices, and multi-approval workflows. - Secure Bridging Between Tiers
Movements from cold to hot are subject to strict governance — dual approvals, time locks, whitelisting, and immutable audit trails. - Monitoring & Rebalancing
Liquidity levels in hot wallets are continuously monitored and adjusted based on activity, ensuring security is never compromised for convenience.
This tiered approach balances operational agility with institutional-grade protection.
Key Security & Governance Considerations
When designing custody infrastructure, institutions must look beyond basic wallet definitions and consider:
- Dual control & multi-approval — Require multiple authorizations before signing, especially in cold environments.
- Whitelisting & velocity limits — Enforce transaction policies at both hot and cold layers.
- Secure signing flows — Ensure offline signing is air-gapped and tamper-resistant.
- Key backups & geographic redundancy — Protect against device loss, natural disasters, or operational failure.
- Comprehensive audit logs — All signing, approvals, and device interactions must be recorded immutably.
- Regulatory compliance alignment — Custody structures should map to relevant frameworks (e.g., MiCA, SOC2, ISO 27001, etc.).
B2Vault’s Tiered Custody Architecture
At B2Vault, we’ve built our custody infrastructure around a hybrid hot-cold model, purpose-built for institutions:
1. Operational Hot Pools
We maintain secure hot wallet environments protected by HSMs, strict network isolation, multi-factor controls, and real-time monitoring. Only a limited portion of assets resides here, calibrated to meet daily liquidity demands.
2. Strategic Cold Vaults
The majority of institutional assets are stored in cold vaults — completely offline environments with dual-control procedures, multi-party signing, air-gapped hardware, and robust physical security.
3. Controlled Bridging Protocol
Transfers between hot and cold follow strict policy gates:
- Dual or multi-approvals required
- Whitelisted destinations enforced
- Time-locks and manual verification steps
- Immutable logging of every movement
4. Redundancy & Disaster Recovery
Our cold infrastructure is geographically distributed, with encrypted backup shares stored in multiple secure vaults. This ensures continuity even under extreme scenarios.
5. Institutional Governance
B2Vault integrates granular role-based access control, automated policy enforcement, and compliance reporting — aligning operational flows with regulatory frameworks and audit standards.
Final Thoughts
Hot and cold wallets are not competing technologies — they are complementary components of a mature custody strategy.
- Hot wallets deliver the speed and flexibility required for active operations.
- Cold wallets provide the security foundation institutions rely on for protecting reserves.
- Tiered custody architectures, like B2Vault’s, combine both to meet the demands of modern digital asset management: security, liquidity, governance, and compliance.
As digital assets become increasingly institutionalized, understanding — and correctly deploying — hot and cold wallet strategies will be a critical determinant of operational resilience and trust.
About B2Vault
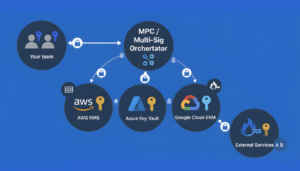
B2Vault is a crypto custody platform built for institutions. Leveraging multi-party computation (MPC), tiered wallet architecture, and enterprise-grade security, we provide flexible, compliant, and scalable custody solutions for digital assets.
- Introduction: why key management matters for institutional crypto custody
- What Is Multi-Signature (Multi-Sig)?
- What Is MPC (Threshold / Multi-Party Computation)?
- Comparison: Multi-Sig vs MPC (Institutional Lens)
- Hybrid & Complementary Models
- Why B2Vault Favors / Supports (Your Approach)
- Guidance: When to Choose Which?
- Conclusion & Takeaways