Custodial vs Non-Custodial Wallets: Institutional Considerations Beyond the Basics
The phrase “Not your keys, not your coins” has become a rallying cry in the crypto world. But for institutions managing millions—or even billions—of dollars in digital assets, the decision between custodial and non-custodial wallet structures isn’t just ideological.
It’s about regulatory compliance, governance, security design, and operational resilience.
In this article, we break down the core differences, examine their implications for institutional operations, and show how hybrid custody models, like those offered by B2Vault, can deliver the best of both worlds.
What Is a Custodial Wallet?
A custodial wallet is one where a third party (custodian) holds and manages the private keys on behalf of the end user or institution.
When you use a custodial wallet, you’re delegating the responsibility for key management—and often transaction execution, security, and recovery processes—to another entity.
Key characteristics of custodial wallets:
- The custodian holds the private keys and manages the wallet infrastructure.
- The user/institution has account-level access, not direct control over the underlying keys.
- Custodians often provide additional services: insurance, compliance checks, transaction monitoring, reporting, and customer support.
- Access and withdrawals typically require authentication through the custodian’s systems (e.g., logins, API keys, approval workflows).
For retail users, examples include exchange wallets (e.g., Kraken, Gemini), and institutional custodians such as BitGo or Anchorage.
For institutions, custodial wallets are often selected to outsource operational burden, satisfy regulatory requirements, and access insurance-backed infrastructures.
👉 Kraken frames custodial wallets as solutions where users rely on the custodian’s “expertise and infrastructure,” but must trust them with key control.
👉 BitGo highlights their security layers, compliance standards, and multi-sig architecture as institutional custodial strengths.
What Is a Non-Custodial Wallet?
A non-custodial wallet is one where the user or institution retains full control of the private keys—and therefore, full responsibility for security, recovery, and transaction execution.
Key characteristics of non-custodial wallets:
- The user controls the private keys directly (via hardware devices, software wallets, or MPC frameworks).
- No third party can move assets without the owner’s participation.
- Users are responsible for backup, recovery, and access control.
- Non-custodial wallets enable true self-sovereignty, but demand robust internal security practices.
For retail users, non-custodial typically means Ledger or MetaMask: the individual writes down their seed phrase and manages security personally.
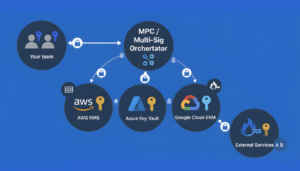
For institutions, non-custodial custody often involves dedicated key management systems, multi-party computation (MPC) frameworks, hardware security modules (HSMs), and strict internal governance.
👉 Ledger markets their devices as giving users “full control,” while Gemini’s educational content notes that this also means full accountability for losses.
Institutional Comparison: Custodial vs Non-Custodial
| Dimension | Custodial Wallet | Non-Custodial Wallet |
| Key Ownership | Held by third party (custodian) | Held directly by user/institution |
| Security Responsibility | Custodian secures keys | Institution manages own security stack |
| Regulatory Alignment | Often preferred in regulated markets (outsourced compliance, insurance) | Requires internal compliance framework and clear governance |
| Operational Control | Limited — subject to custodian’s processes | Full — institution sets policies and controls |
| Speed & Flexibility | Depends on custodian workflows | Potentially faster, but depends on internal tech |
| Recovery & Backup | Managed by custodian | Institution must design and maintain recovery |
| Counterparty Risk | Custodian insolvency or breach is a factor | No third-party counterparty risk |
| Internal Governance Needs | Low (outsourced) | High (must implement signing policies, RBAC, audits) |
| Transparency | Dependent on custodian’s reporting | Full on-chain visibility and internal logs |
Why Many Institutions Choose Custodial Solutions
Institutional custodial wallets have grown rapidly because they offer:
- Regulatory recognition and licensing (e.g., MiCA, SOC2, trust charters)
- Insurance coverage for stored assets
- 24/7 support, recovery, and operational continuity
- Integrated compliance and AML monitoring
- Easier onboarding for organizations without cryptographic expertise
For some institutions—especially regulated funds, payment providers, or fintech platforms—using a licensed custodian is not just a preference; it’s a requirement.
Why Some Institutions Prefer Non-Custodial Control
On the other hand, many institutions are increasingly moving toward non-custodial models powered by MPC (multi-party computation) and enterprise key orchestration. This shift is driven by:
- Eliminating counterparty risk — no dependency on a custodian’s solvency or security posture
- Maintaining regulatory independence — institutions keep ultimate control over their assets
- Custom governance — build signing policies, roles, and workflows that reflect the organization’s structure
- On-demand liquidity — direct control means faster access without waiting for custodian approval
- Multi-chain flexibility — MPC wallets can support various chains without relying on a custodian’s roadmap
However, this comes with the need for serious internal controls: robust key management infrastructure, strict role-based access, redundancy plans, and regular audits.
Hybrid Models: The Emerging Middle Ground
The binary between custodial and non-custodial is fading. Modern institutional custody increasingly blends both approaches:
- Self-custody for treasury / reserves, with MPC + HSM infrastructure managed by the institution
- Third-party custodial services for specific use cases, such as client segregation, regulated operations, or insurance coverage
- Delegated models, where institutions maintain technical key control but outsource compliance monitoring or transaction execution to specialized partners
This hybrid custody model allows institutions to retain control over critical assets while leveraging custodial infrastructure for compliance, settlement, or operational support.
B2Vault’s Approach to Custodial vs Non-Custodial
At B2Vault, we believe institutions shouldn’t have to choose between control and compliance.
Our platform provides:
- MPC-based non-custodial infrastructure, giving institutions full control over their keys while eliminating single points of failure.
- Policy-driven governance layers — multi-approval workflows, role-based access control, whitelisting, and audit trails.
- Optional custodial partnerships for regulated jurisdictions, insurance-backed storage, or operational outsourcing.
- Hybrid architecture that allows segmentation of assets between self-managed vaults and custodian-managed accounts, based on your risk profile.
Whether you’re a fund managing treasury, a payment company processing client flows, or a crypto-native firm scaling operations, B2Vault gives you the flexibility to define your custody model on your terms.
Final Thoughts
The choice between custodial and non-custodial wallets is not just a technological decision — it’s a strategic governance choice.
- Custodial wallets offer simplicity, compliance, and insurance, but involve trusting a third party.
- Non-custodial wallets offer control, flexibility, and sovereignty, but require strong internal security and governance.
- Hybrid models, like B2Vault’s, combine both worlds, letting institutions retain control while leveraging external infrastructure where it matters.
In the institutional world, the smartest custody strategy is the one that blends security, compliance, and operational excellence.
About B2Vault
B2Vault is a next-generation digital asset custody platform built for institutions. By combining MPC cryptography, tiered custody architecture, and enterprise-grade governance, we help organizations securely manage their digital assets across multiple jurisdictions and chains.
- What Is a Custodial Wallet?
- What Is a Non-Custodial Wallet?
- Institutional Comparison: Custodial vs Non-Custodial
- Why Many Institutions Choose Custodial Solutions
- Why Some Institutions Prefer Non-Custodial Control
- Hybrid Models: The Emerging Middle Ground
- B2Vault’s Approach to Custodial vs Non-Custodial
- Final Thoughts
- About B2Vault