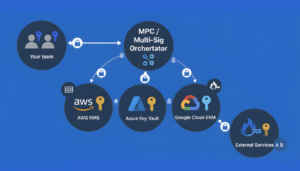
MPC vs Multi-Sig: Choosing the Right Key Management for Institutional Crypto Custody
In the world of digital assets, protecting private keys is not just a technical concern—it’s a business imperative. One wrong move, one compromised key, and an entire treasury could vanish. For institutions managing crypto assets, the question isn’t just “how do I hold keys securely?” — it’s “how do I do so in a way that scales, evolves, and meets governance demands?”
Two leading paradigms dominate institutional key management today: multi-signature (multi-sig) and multi-party computation (MPC) (also known as threshold signature schemes). While several industry writeups compare thefm broadly, we offer here B2Vault’s institutional lens, candid tradeoffs, and practical guidance.
What Is Multi-Signature (Multi-Sig)?
A multi-signature scheme is a well-established approach: instead of one private key, a wallet can require M of N independent keys (or “cosigners”) to approve a transaction. For example, a 3-of-5 multi-sig means any 3 distinct signers (out of 5) must sign.
How it works (simplified):
- Each cosigner holds a full private key (distinct keys).
- When a transaction is to be sent, a proposal is created and distributed.
- Each cosigner individually computes their signature.
- Signatures are aggregated (or included) and broadcast to the blockchain.
- The blockchain’s validation logic verifies that the requisite number of valid signatures exist.
Strengths of multi-sig:
- Simple conceptual model, well understood, long history.
- Transparent: you know exactly how many and whose signatures will be needed.
- On-chain enforcement: the smart contract or protocol enforces the signing rules (e.g. the “M-of-N” logic).
- Mature tooling and broad adoption (especially in Bitcoin, Ethereum, etc.).
Limitations / challenges:
- Rigidity in the threshold & signers: once a multi-sig address is deployed, changing M or N typically requires constructing a new wallet/address.
- Operational friction: adding/removing cosigners, key rotation, handling signer failure or exit require careful planning (and often manual migration).
- Blockchain dependency & variance: different chains support multi-sig differently; some chains don’t support it at all, or with limited flexibility.
- On-chain footprint and cost: signatures and scripts can increase transaction size and gas costs (especially when multiple signatures are needed).
- Privacy and exposure: every signature is exposed on-chain; observers can deduce which keys participated and deduce quorum rules.
- Single-key compromise risk per cosigner: each cosigner’s private key is a point of vulnerability.
Several industry sources warn that multi-sig architectures can become operational bottlenecks as organizations grow. (Fireblocks)
What Is MPC (Threshold / Multi-Party Computation)?
MPC (multi-party computation) refers to cryptographic protocols that allow multiple parties to jointly compute a function (e.g. sign a transaction) without any party revealing its private input. In the context of key management, MPC is used to split a private key into shares (often via secret-sharing or threshold schemes) such that a subset (the “threshold”) of shares can generate a valid signature—but no party ever reconstructs the full key in one place.
How it works (high level):
- During setup, the private key is logically “shared” among parties (devices, HSMs, servers), without any party ever seeing the full key.
- To sign a transaction, an MPC protocol coordinates between parties: each party computes a partial signature based on its share and broadcasts (securely) intermediate values.
- These partial results are combined (often off-chain) to form a full valid signature.
- The signature is submitted to the blockchain as if it came from a “normal” key. The blockchain sees no difference between an MPC signature and a normal signature.
Unlike multi-sig, the blockchain sees only one signature and doesn’t see the internal signing process or how many parties contributed. This gives key sequence privacy. (Many industry analyses point this out as a unique advantage of MPC over multi-sig) (CoinGecko)
Strengths of MPC:
- Flexibility of thresholding and signer changes: you can often adjust the required threshold or change participants without needing to create a new wallet/address.
- Better scalability and performance: signature aggregation is done off-chain, reducing transaction size, gas cost, and latency.
- Privacy / obfuscation: blockchain sees only one signature; internal structure is hidden.
- Protocol-agnostic potential: well-designed MPC systems can support signing across multiple chains with compatible cryptographic curves (e.g. ECDSA, EdDSA).
- Reduced on-chain complexity and dumb contracts: fewer complex on-chain scripts means fewer risks of smart contract bugs.
- Improved resilience to insider threats: even a malicious or compromised party cannot unilaterally reconstruct the key.
Limitations / challenges:
- Complexity of protocol implementation: building a secure, efficient, audited MPC system is nontrivial and requires deep cryptographic expertise.
- Trust in the MPC provider / stack: you must trust that the provider’s implementation, network, and operational controls are robust.
- Recovery and backup: if too many participants fail or lose their shares, recovery can be difficult—though good systems build in redundancy and recovery mechanisms.
- Latency / coordination overhead: parties must coordinate (communicate) during signing; in a poorly engineered system, this can add delay.
- Interoperability gaps: while MPC is theoretically protocol-agnostic, in practice supporting many blockchains may require engineering work per chain.
Many institutional custody providers now present MPC as “next-gen” and superior to multi-sig for scaling operations. (Fireblocks)
Comparison: Multi-Sig vs MPC (Institutional Lens)
Below is a comparative view, focused on what matters for custodians, funds, exchanges, and institutions:
Dimension | Multi-Sig | MPC |
Security / Threat Model | Transparent, well understood. But each cosigner is a potential attack surface. | The full private key is never reconstructed; internal signature shares are not exposed. |
Flexibility / Upgrades | Threshold and cosigners are fixed after setup; changes require redeployment. | More dynamic: thresholds and participants often modifiable. |
Operational Complexity | Managing cosigners, key rotation, signer failure, and migration is cumbersome. | Coordination required, but many processes can be automated or abstracted by the MPC system. |
Transaction Cost & Latency | Larger signature scripts, multiple signatures => higher gas and slower confirmation. | Off-chain aggregation yields smaller transactions; lower gas, faster confirmations. |
Privacy / On-chain Exposure | Signer identities and quorum rules are visible on-chain. | Only one signature is broadcast; internal structure is hidden. |
Multi-Chain Support | Must support multi-sig per chain; some chains lack native multi-sig. | With shared cryptographic primitives, one MPC engine can cover multiple chains. |
Recovery & Redundancy | Can distribute redundant keys but recovery planning is manual. | Good MPC systems plan for backup shares, resharing, and loss tolerance. |
Audit, Compliance & Governance | Transparent flows, audit logs, well understood models. | Requires governance over participants, access logs, but can be designed to satisfy compliance. |
Maturity & Ecosystem | Mature tooling and broad adoption across blockchains. | Growing adoption; the strongest players have audited systems, but fewer decades of history. |
From an institutional perspective, the value lies not only in theoretical security but in operational resilience, policy agility, audit trails, regulatory compliance, and cost predictability.
Hybrid & Complementary Models
It’s not always a strict “either/or.” Institutions sometimes layer hybrid models or fallback systems:
- MPC + multi-sig fallback: You use MPC for day-to-day operations, but a multi-sig cold storage as a fallback in disaster recovery scenarios.
- Tiered custody: Higher-value, rarely moved assets stored in multi-sig vaults, while active treasury operations route through MPC.
- Ancillary multisig wrappers: Some systems may embed additional multisig constraints at higher abstraction (e.g. requiring a committee approval before triggering MPC sign).
These hybrid designs aim to balance the benefits of both models while mitigating their drawbacks.
Why B2Vault Favors / Supports (Your Approach)
Here you can articulate your unique value, but to make the article coherent, here’s a suggested positioning (you should adapt to your actual implementation and strengths):
- Security-first cryptography with operational flexibility
At B2Vault, we adopt an MPC architecture that ensures the private key is never assembled in full, while providing governance tooling that lets institutions adjust thresholds, add or retire participants, and manage backups with ease. - Multi-chain, interop-ready architecture
Our MPC layer is built to support ECDSA / EdDSA-based chains, so institutions can use a unified signing engine across Ethereum, BSC, Avalanche, Solana (or others, depending on curve compatibility). This eliminates the fragmentation that traditional multi-sig often forces. - High-performance signing with minimal latency and cost
Because MPC aggregation happens off-chain, our on-chain footprint is minimal. That means lower gas costs, faster confirmations, and predictable behavior under heavy load. - Robust governance, auditability, and compliance support
We bake in role-based controls, detailed audit trails of share usage, and strict separation of duties. Institutions can generate compliance reports, monitor share activity, and enforce policies around who can propose, approve, or override. - Resilient recovery & dynamic resharding
B2Vault’s MPC engine includes built-in resharing, backup shares, dormancy thresholds, and recovery paths so that even in the event of participant failure or device loss, the system can restore signing capabilities without rebuilding entirely from scratch. - Transparent risk modeling & third-party audits
We subject our MPC protocols and implementation to independent cryptographic audits, publish risk models, and provide “key compromise” simulations so customers can understand threat exposures. - Seamless integration into institutional workflows
Our SDKs, APIs, and custody platform abstract away the cryptographic complexity: institutions can enforce multi-step approvals, multi-geography approvals, delegation, whitelisting, and automated flows without worrying about low-level signing details.
By combining MPC’s flexibility and privacy with operational tooling, B2Vault offers a custodian-grade solution that addresses not just cryptographic security, but the broader institutional requirements of governance, compliance, recovery, and usability.
Guidance: When to Choose Which?
- If your use case is simple, small, and low-touch, a mature multi-sig setup may suffice.
- If you expect your operations, team, or treasury to scale, or need agile governance changes, MPC is likely preferable.
- If you want unified cross-chain signing, MPC gives you fewer silos.
- If your priority is maximum transparency and you prefer the “on-chain enforceability” of multi-sig, then multi-sig still holds appeal (especially for proof-of-custody arguments).
- If you need extreme isolation or want a completely air-gapped fallback, combining multi-sig cold vaults with MPC hot signing can offer layered defense.
In practice, many modern institutions are moving toward MPC (or hybrid designs) because it better meets the demands of evolving business, compliance, and security at scale.
Conclusion & Takeaways
- Both multi-sig and MPC fundamentally improve over naive single-key custody, but they make different tradeoffs.
- For institutional operations, the differentiators often lie not in micro performance but in flexibility, agility, recovery design, and governance tooling.
- An MPC-based or hybrid model often delivers better scalability, privacy, and cross-chain support, provided the implementation is robust and audited.
- When choosing a custodian or building in-house, evaluate not just the cryptographic primitive, but the end-to-end platform: policy controls, audit logs, backup / recovery, compliance support, SDKs, and operations.
- Introduction: why key management matters for institutional crypto custody
- What Is Multi-Signature (Multi-Sig)?
- What Is MPC (Threshold / Multi-Party Computation)?
- Comparison: Multi-Sig vs MPC (Institutional Lens)
- Hybrid & Complementary Models
- Why B2Vault Favors / Supports (Your Approach)
- Guidance: When to Choose Which?
- Conclusion & Takeaways